I guess when a hacker learns a language it is different from the way “others” do that. I guess this, because I think I’m a hacker, I’m learning a language and it feels different. I see two main factors coming in the picture:
- I’m connecting things in my life, so the things I do usually need some motivation or purpose behind them, without which they are abandoned. The activities I keep up the best are the ones that connect multiple different things.
- I want to do things as efficiently as possible. Hack the tools, hack the process to make it better. If there are no tools, make some. If no processes, come up with ideas.
Okay, these are pretty vague expressed like this, now let’s give the example that prompted this post: I’m learning Chinese. Living in Taiwan for two and a half years now, so “high time” doesn’t even start to describe it. Finally I got a tutor, and a good one at that, so twice each week I have a good session of chatting and learning. After each of the sessions we have at least 30 or 40 new words and expressions written down. Those would normally be just forgotten, so I take an effort (about another hour or so after the session) to type them into a Google Document, this very one on the picture:
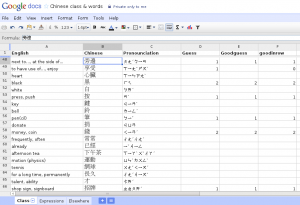
Enter the English expression, the Chinese original and the pronunciation in Bopomofo (which I prefer to Pinyin). This last is possible because of Yahoo Chinese-English Dictionary (one service that is generally better than Google’s own Translate, though I frequently need to use both). The other three columns I’ll came in just recently.
At the moment I’m up to 307 expressions, and that’s just not possible to practice from a spreadsheet like that. I remembered, though, checking out a fellow StartupBus participant, Pamela Fox‘s Google Spreadsheet Flash Cards some time ago. It was fun but followed a different logic than me so couldn’t make complete use of it. But then: why not make a new practice system for myself? This goes back to the precious points: 1) connecting programming and languages – in both I’ll learn something new and they’ll reinforce each other’s motivation, 2) use the exact tools that I need even if I have to make them (because it’s possible to do).
Also after having done Who Said That? (that is currently down due to the AWS fail), I was into guessing games: let’s make a vocabulary guessing practice app that uses the above spreadsheet that I have anyways. What format it should be? Well, for the very first test, to see how to interact with Google Docs and such, just made it as a simple, console-based python app, something like this:
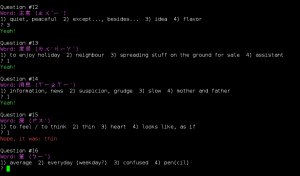
Each practice round has 30 questions, randomized, 4 possible solutions, with the pronunciation as hint. Simple, though very ugly in the inside at the moment (here’s the repo, I still need to write a ReadMe). It works and now I know what to look out for in terms of implementation (how to log in, how to get and update data, stuff like that).
The other 3 columns in the above spreadsheet are explained as well: they are keeping score such as the total number of times a word/expression is practiced, the number of good answers and the number of current good-answers-in-a-row. These provide a rough-and-ready way to diagnose and manage the learning process – until I come up with better ways. Anyway, right now I get about 50%-70% good which is more than I expected, but still a lot more room for improvement.
A list of improvements to the program that I’m thinking about:
- Making it into a site, so I can use my phone on the go to practice. Also, potentially others can use it as well to practice anything based on any spreadsheet with “one side – other side – hint” structure.
- I’m pretty sure this whole things could be done in a single Javascript powered page. I don’t know enough Javascript to pull it off yet, but I’ve seen that all the components separately, and that would make a very portable and compact solution.
- Need to figure out some easier setup of the spreadsheet if this is to be used by others later. I cannot rely on them understanding what they way I was thinking. Maybe in-app option to add more fields?
- I remember reading somewhere that the most effective practice is that I reduce the frequency of checking words that I know well. That’s where the last column comes in: as one has more right answers in a row, one can tast that word/expression fewer times. If there’s a mistake then go back to the original method and test it more until score builds up again. This can potentially be a very complicated algorithm, I got to think of a way that scales well (ie. it is not too bad compared to an ideal method but does not require extensive amount of calculation). Have some ideas, but they need more polish.
- After watching Salman Khan’s TED talk this year it grabbed me just how much information is there in one’s actions (they do amazing feedback to teachers on how the students study), how much better you can understand why did people what they did if you have all those diagnostic information (ah, the temptation of Big Data:). To apply this idea of extended diagnostics I could have a logging system instead of keeping (a simple) score. From there the system could get: how much you practice, how are you doing / getting better, what are easier or more difficult words for you, what two words you mistake with one another, suggest things to practice more, suggest words from topics that you know well to extend your knowledge… And more (this was just a little brainstorming). I don’t think I’d have time to extend it like that, and ideas are a dime a dozen, but one never knows…
- Adding more modes of learning not just multiple choice, multiplayer learning, more game mechanics (achievements, pins anyone? :)
- If there are central datasets instead of self-provided ones, then the system can anticipate what are the difficult parts from other students’ performance before you.
Now, let’s just see how will my Chinese improve during all this hacking, since that’s the main point, isn’t it? :)

Ps: If you have any language learning tricks, let me know in the comments!